Secure IT - Firewall, WiFi & More
Winscape IT provides professional 24/7/365 services to businesses around the globe. Our services can be scaled to meet the needs of any business. Some of the security services we provide include.
Cyber Incident Response
Organizations must respond quickly to active threats to ensure threat actors are not able to achieve their objectives. With our Cyber Incident Response service, we provide rapid assistance with our global security team of remote incident responders and threat analysts.
Triage starts within hours, with most customers starting the recovery phase in 48-hours or less. Our Cyber Incident Response is available for both new and existing customers.
The benefits of our Cyber Incident Response service include:
- 24-hour monitoring
- Immediate response
- Detailed investigations
- Identification, containment, and eradication of threats
How it Works
Our cyber security team starts by establishing a communication schedule, cadence and prioritized requirements and recommended actions. For identification and containment, we apply remedial actions from a defined and proven playbook, and acquire vital artifacts to prevent further damage to your estate.
To ensure eradication and full recovery, we safely restore critical systems back into production by patching, hardening and applying real time EDR/XDR response services. Lastly, we review forensics evidence to strengthen your security posture, and use it for post incident analysis and service enablement
Cyber Threat Neutralization
Our Cyber Incident Response team is part of global, world class, 24/7 threat hunting, detection, and response Security Operations Center (SOC) that proactively hunts, identifies, investigates, and responds to threats on behalf of our customers as part of our award-winning Secure IT portfolio of Managed Services.
Defense Against Threats
Once the incident is resolved and the threat to your organization is neutralized, we will transition you to our global, best in class EDR/XDR platform, providing real-time proactive threat detection, and response. Should threat actors re-emerge or new threats present themselves, we will be prepared to respond. We will continue to defend your assets for a full 30-days as part of our incident response service.
Detailed Forensics Reporting
We will provide a detailed forensics summary report of our investigation including discoveries made, actions we took and a strategic roadmap of how to mitigate the recurrence of similar threats in the future.
Secure Your Environment
Our cloud-based security platform has been purpose-built to offer rapid deployment to all of your assets by our team of cybersecurity response engineers. This ensures that whether your environment is small or large, we can rapidly secure your estate giving you the confidence that your environment is prepared to defend against further threats.
Endpoint Detection and Response
Secure IT - Endpoint Detection and Response (EDR) delivers differentiated endpoint protection by preventing, detecting and acting on ever-changing threats, allowing for a quick recovery when exploitations, such as ransomware, occur. We offer resource-efficient autonomous agents for Windows, Mac, Linux, and Kubernetes and support various form factors, including physical, virtual, VDI, customer data centers, hybrid data centers, and cloud service providers. Secure IT ®Endpoint Detection and Response is powered by SentinelOne.
Our Endpoint Detection and Response service provides:
- Full endpoint protection
- Data-driven analytics
- Professional support
- Autonomous threat response
Integration
Secure IT Endpoint Detection and Response (EDR) is designed to rapidly deploy protection to your endpoints. We use industry best practices with customized security policies and processes that respond to evolving threat actors that target endpoints. Our deployment team works hand in hand with your staff to assess, design and deploy the solution to deliver advanced security services from day 1 with minimal impact to users. In addition to delivering timely support solutions with a more intimate understanding of your environment, our service offers in-house expertise for day-to-day management of security operations and tailored program guidance — all with your success in mind.
Firewall
Secure IT - Firewall is an award-winning Security Event Monitoring and Management service that includes next-generation firewall(s) designed to protect your network’s infrastructure. Added benefits to our firewall solution include: improved site-to-site connectivity, application-specific rules, built-in SD-Wan capabilities and central administration of network/security operations for your business.
The service includes the deployment of next-generation firewall(s) to your premises. All deployed firewalls can be managed from a single console, with one view assisting administrators in
management and reporting.
- With our Firewall security services, businesses receive:
- Monthly reports
- Security and performance alerts
- Flexible hardware integration
These devices are configured to meet the network access and security requirements of your organization and provide near real-time alerting on threats. These threats are filtered through our Network and Security Operations Centre (NSOC) for live agent analysis and remediation.
Integration & Next-Generation Firewall
Secure IT - Firewall is designed to integrate seamlessly into Barracuda, Cisco Meraki or Fortinet firewalls. Upon integration with your firewall, the service provides instant security through our SIEM and live security agents. The service is attached to the firewall remotely through our Network Operations Centre.
A Next-Generation Firewall has the same benefits as a traditional firewall that operates on the 7 layers and presents enhanced capabilities that allow real-time protection against malware, vulnerabilities and network attacks. Intelligent analysis allows for deep application context, which allows administrators to determine how applications within the network are being used.
Secure IT Firewall service also contains years of Hybrid Intelligence that combines both human and machine learning to apply rules to specific applications and other functions to allow or deny traffic.
Available add-ons include OT Specific Inspection and IOT Detection Service.
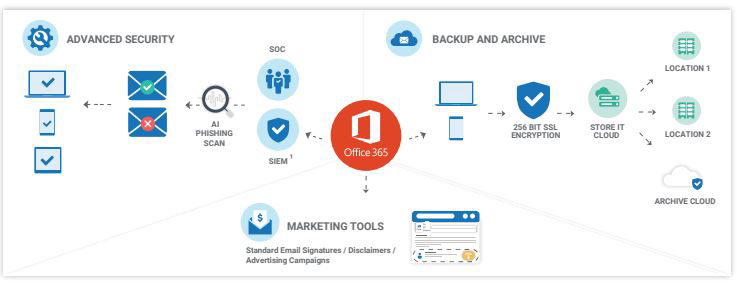
Office 365 & Mailing Security
Secure IT - Mail is a fully managed solution for organizations that have made a move to Office 365, with tools available to enhance or add security, backup, archiving, and marketing tools. This email solution is deployed, configured and managed by our product specialists according to industry best practices. Organizations can choose from four different email packages.
The advanced security package includes advanced email protection with powerful tools that scan your email tenant for phishing and malware. AI-based threat detection protects inboxes from spear phishing. We also forward email event logs to our Security Information and Event Management (SIEM), where suspicious or malicious events are sent to our Security Operations Centre (SOC) analysts for review and remediation.
The comply package combines the advanced security features with backup and archiving to ensure emails are always available. Lastly, our complete package includes the previously mentioned features and marketing tools integrated into Office 365
Our security services provide:
- Detailed security reports
- Advanced security support
- Flexible deployment options
- Siem Integration
Integration
The integration process with your Office 365 tenancy is secure and straightforward. Secure IT - Mail will request authorization from your Office 365 Administrator to create a linked connector. The Administrator will then be required to accept the connection in the Office 365 permissions page. Once approved, our deployment team will work collaboratively with your organization to enable and configure the right tools according to your requirements.
SecureIT Mail vs Office 365
Secure IT - Mail provides a comprehensive suite of security, backup, management and marketing solutions available for organizations that have made the move to Office 365. This packaged email solution is deployed, configured and managed by our product specialists according to industry best practices.
Protect your email with powerful tools that scan your email tenant for phishing and malware. We also forward email event logs to our Security Information and Event Management (SIEM) where suspicious or malicious events are sent to live agents for review and remediation if required.
In addition, you can securely backup your email and create email marketing campaigns that can be tracked for engagement.
User Defence
Secure IT – User Defence is a suite of security services that are specifically tailored to empower your employees to
become the first line of defence against cyber attacks. This suite of integrated and ongoing services provides a turnkey solution that allows for rapid integration into your IT environment.
The services in our solution include ready to implement comprehensive cybersecurity awareness training, simulated phishing attacks to test employee knowledge/best practices and real time dark web intelligence tools that hunt for leaked user credentials. Track and measure performance using regular user defence reports that demonstrate the overall cybersecurity posture of your employees.
Bolster your defence from cyberattacks with our:
- Cybersecurity and training materials
- Employee training sessions and tests
- Compromised password detection
- Security reports
Integration
Secure IT – User Defence easily integrates with an organization’s Azure Active Directory or LDAP to determine the required user information.
Each aspect of the solution is then setup during the onboarding process. Our deployment team works hand in hand with your staff to assess, design and deploy the solution to deliver the solution with minimal impact to users.
WiFi IT Security
Secure IT - WiFi provides one of the most comprehensive turnkey solutions for the delivery of WiFi services. This includes wireless access points, licensing, configuration, management and advanced security information and event analysis, including threat detection and remediation.
Secure IT - WiFi is simple to deploy and easy to manage. It comes with no up-front purchase fees and gives customers a secure wireless solution with 24/7 security event management for one flat monthly fee.
Our wifi security provides businesses with protection benefits, including:
- Leading-edge technology
- Real-time security analysis
- Custom configuration and management
- Professional IT support
Integration
Secure IT - WiFi is designed to integrate seamlessly into any IT environment. The installed Cisco Meraki access points and switches are configured to run through the SIEM service. The SIEM service is bundled with our 24/7 operations centre for essential protection and monitoring.
Full Management
Leverage a team of subject matter experts using industry best practices to manage the WiFi solution from end to-end including: management of all access points, backup of access point configuration to a secure cloud, monitor access point logs and alert notifications, troubleshooting and remediation activities and monthly consolidated reports on WiFi service.
Advanced Security Analytics
The WiFi solution is integrated with our SIEM system. Our SIEM uses sophisticated machine learning to determine if a threat is taking place by analyzing security events within your environment. Suspicious activity is reported in real time to live security agents for further analysis and action, including termination of the connection or threat to protect the customer’s infrastructure.
Leading Edge Technology
Built using the Cisco Meraki platform, this service includes all the benefits of leading-edge hardware right out of the box. This includes Centralized Management, Automatic RF optimization, High Capacity 802.11ac radios and Application Visibility/Control.
Addons include Required Cabling, Radius Integration, Secure IT POE Switch/Injectors and more.
If you are interested in our IT Security Services, contact us.
